A rational quantum state sharing protocol with semi-off-line dealer
Hua-Li Zhang(張花麗) Bi-Chen Che(車碧琛) Zhao Dou(竇釗) Yu Yang(楊榆) and Xiu-Bo Chen(陳秀波)
1Information Security Center,State Key Laboratory of Networking and Switching Technology,Beijing University of Posts and Telecommunications,Beijing 100876,China
2School of Cyberspace Security,Beijing University of Posts and Telecommunications,Beijing 100876,China
Keywords: rational quantum state sharing,game theory,semi-off-line,Nash equilibrium
1. Introduction
The classical secret sharing(SS)protocol is used to share the secret among multiple players.[1–4]Each player reconstructs the shared secret by a certain number of shares(e.g.at leasttshares)from other players. The quantum secret sharing(QSS) protocol is also used to share the secret among multiple players. Unlike the SS protocol, the QSS protocol can share the quantum information as well as classical information, while the SS protocol can only share classical information. The QSS protocol for sharing quantum information is also called the quantum state sharing (QSTS) protocol or the quantum information splitting(QIS)protocol. Because of the quantum no-cloning theorem,only one player Charlie can obtain the quantum state shared by the dealer Alice. But Charlie needs the help of all the other players due to the correlation of entangled states. Especially,according to the authorities of the players, the QSTS protocol can be divided into hierarchical QSTS (HQSTS)protocol[5–9]and non-hierarchical QSTS(NQSTS) protocol.[10–14]And in this paper, the NQSTS protocol is discussed.
In 1999,Cleveet al.[10]firstly proposed a QSTS scheme with quantum error correction codes.[11]Later, Liet al.[12]proposed a QSTS protocol based on entanglement swapping.Lanceet al.[13]investigated a (2, 3) threshold QSTS protocol based on continuous variable tripartite entanglement.Then,multiparty QSTS of an arbitrary two-particle entangled state was investigated in Denget al.’s,[14,15]Liet al.’s,[16]and Liuet al.’s[17]protocols. In 2005, Zhanget al.[18]proposed a QSTS protocol for continuous variables by two-mode squeezed state and single-mode squeezed state. Muralidharan and Panigrahi[19]designed a QSTS protocol based on a fiveparticle entangled state.[20]There are also QSTS protocols by cluster states.[21–25]In 2013,Jiang and Dong[26]proposed a multiparty QSTS protocol of an arbitrary multi-qubit state based on various probabilistic channels. Wanget al.[27]investigated a multiparty QSTS scheme of an arbitrary known qubit under two noisy environments. In 2017,Cao and Ma[28]presented a (t,n) threshold QSTS scheme based on linear equations and unitary operation. Later,the first verifiable threshold QSTS scheme was proposed by Cao and Ma.[29]In 2020,Songet al.[30]studied a verifiable(t,n)threshold QSTS scheme on IBM quantum cloud platform.
With more extensive and further research on cryptography,the rational SS(RSS)protocol has been proposed according to the actual needs.[31–36]In the RSS protocol,players are not honest or destructive, but rational, executing their strategies to maximize their utilities. The game theory is introduced to analyze the behavior of the players. Correspondingly, the rational QSTS(RQSTS)protocol was also explored. In 2015,the first RQSTS protocol was proposed by Maitraet al.[37]They respectively demonstrated a(t,n)RQSTS protocol with the semi-off-line dealer and the off-line dealer by Calderbank–Shor–Steane (CSS) code. In 2018, Douet al.[38]proposed a rational QSTS(RQSTS)protocol with the online dealer. Qinet al.[39]proposed an RQSTS protocol based on the quantum Fourier transform.
In this paper, we propose an RQSTS protocol with the semi-off-line dealer inspired by Refs. [15,38]. First of all, in our protocol,the EPR pairs and GHZ states are used to share an arbitrary two-particle entangled state between the dealer and the rational players. Instead of the dealer in Ref. [15],the EPR pairs are prepared by player Charlie. Charlie is responsible for reconstructing the shared quantum state. So our protocol reduces the workload of the dealer. Secondly, the dealer Alice does not know the shared quantum state,[37]so she cannot clone the state. Ultimately only one player Charlie can reconstruct the quantum state.Moreover,Charlie is jointly elected by all players, rather than designated by the dealer Alice,[37]which also guarantees the fairness of the protocol.Finally,compared with the protocol in Ref.[38],the dealer is of semi-off-line in our protocol, meaning that the dealer only needs to interact with the players twice: The first is to publish the number of rounds and the second is to publish the revelation round and the measurement results. Thus our protocol considerably reduces the information exchanging between the dealer and the players. In addition,our protocol also satisfies correctness, security and strict Nash equilibrium required by RQSTS.
The rest of this paper is organized as follows. In Section 2, we introduce the quantum states and quantum operators related to our protocol, the QSTS protocol proposed by Denget al., and basic game theory knowledge. In Section 3,our rational quantum state sharing protocol with the semi-offline dealer is proposed in detail. In Section 4, our protocol is proved to achieve security, fairness, correctness, and strict Nash equilibrium. Finally, some conclusions are drawn and future work is also mentioned in Section 5.
2. Preliminaries
Because the players are rational in our protocol,both the QSTS and the game theory will be introduced in this section.
2.1. Quantum states and quantum operators
2.1.1. EPR pairs

2.1.3. Pauli operators
The Pauli operators represented by the computational basis are
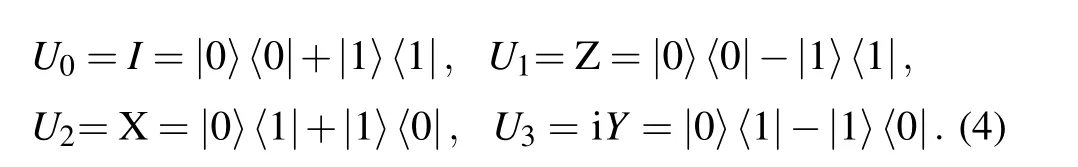
2.2. Review of Deng et al.’s QSTS protocol
In Denget al.’s protocol,[15]it is supposed that there is a dealer Alice and(n+1)players Bobi(1≤i ≤n+1). And the two-particle entangled state|Φ〉xyis


2.3. Game theory



3. Rational quantum state sharing protocol with semi-off-line dealer
In our protocol,there is a dealer Alice and(n+1)players Bobi(1≤i ≤n), and the quantum shared by Alice is|Φ〉xyas indicated in Eq.(5). The detailed process of rational quantum state sharing protocol with the semi-off-line dealer is as follows.
3.1. Dealer’s protocol
Since the dealer is of semi-off-line, Alice only needs to interact with the players twice: the first is at the beginning of the protocol and the second is at the end of the protocol.
[D1] Alice determines the number of rounds(r+w)and the real positionraccording to a geometric distributionG(γ),which is completely unknown to the players Bobi(1≤i ≤n+1). The parameterγis determined according to the players’ utilities. Then Alice announces that the players need to perform(r+w)rounds.
[D2] After receiving the sig=1 sent by Charlie in the last round, Alice announces the positionrof the real revelation round. If Charlie pays the cooperating players Bobi(1≤i ≤n+1, i/=s′) in ther-th round, Alice will perform the joint measurements of the(n+2)-particle GHZ states according to the remaining particles sent by Charlie. Then, Alice announces the measurement results. Otherwise, Alice aborts the protocol.
3.2. Player’s protocol
The process of each player in thej-th round (1≤j ≤r+w)is as follows.
[P1] Each player Bobipublishes an integerpi(1≤i ≤n+1) at the same time. If any player does not publish it, he cannot participate in this round nor the remaining rounds of the protocol.

[P5] Charlie sends the particlesbianddito Bobi(i/=s′).
[P6] Each player Bobi(i/=s′)performsXbasis measurement on particlesbianddiand then publishes the measurement results.
[P7] Charlie judges whether the players Bobi(i/=s′)are cheated based on the measurement results announced by them.Then Charlie publishes the number of the cheating players.These cheating players cannot participate in this round nor the remaining rounds of the protocol.
[P8] Ifj=r+w,Charlie sends a sign sig=1 to Alice.Otherwise,the players finish the current round and proceed to the next round.
[P9] According to the positionrof the revelation round published by Alice,Charlie in ther-th round pays the cooperating players Bobi(i/=s′). And the total remuneration paid to them does not change depending on the number of the cooperating players Bobi(i/=s′). According to the measurement results of Alice and the players Bobi(i/=s′),Charlie will perform corresponding unitary operations on his particlesbsanddsand successfully reconstruct|Φ〉xy.
4. Analyses
4.1. Utilities and preferences
In this protocol,only Charlie in the revelation round can reconstruct the quantum state|Φ〉xy,so the strategies and benefits of Charlie and Bobi(i/=s′)will be slightly different.
(I)The strategies of the players are as follows:
Charlie:
c1Chooses to cooperate
When Alice announces the revelation round,Charlie pays the corresponding remuneration to the players Bobi(i/=s′)who chooses to cooperate.
c2Chooses to cheat
When Alice announces the revelation round, Charlie refuses to pay the players Bobi(i/=s′)who chooses to cooperate.


4.2. Security
A QSTS protocol can be attacked by the eavesdropper or the players,so the security of the protocol is analyzed from the outside attack and the participants’attack.
4.2.1. Outside attack
In the outside attack,the eavesdropper may attempt to destroy or steal the secret message of communication in the protocol.Accordingly,the outside attack is divided into the active attack and the passive attack.
Several active attacks on QSTS include fake-signal attack, entangled additional particle attack, intercept-resend attack, and correlation-elicitation attack.[41–44]Thus a secure quantum channel is set up by the method in Ref.[43],ensuring that the communication between the dealer and the players is not threatened. In short,before the protocol begins,the dealer Alice will conduct security detection,that is,insert the decoy qubits into the qubits sent to the players and publish the location of the decoy particles. Then,the players performXbasis orZbasis measurements on the decoy particles. Finally,Alice compares the measurement results of the decoy qubits published by the player with the initial states of the decoy qubits.If the error rates are lower than the set threshold, the quantum channel is safe; otherwise, Alice will restart the security detection until she is sure that the quantum channel is safe.


According to Eq.(15), Eve cannot steal any information about|Φ〉xy.
For the intercept-resend attack, the eavesdropper intercepts the particles sent to the player by the dealer in the channel. And then the eavesdropper sends the players the particles he prepared. In order not to break the coherence between the players’particles,Eve sends the player 2(n+1)EPR pairs as in Eq. (3), which are prepared by himself. However, he does not know the position nor the quantum state of the decoy particles in the particles sent by Alice,so the error rate will exceed the threshold and be detected by Alice.
In the passive attack,the QSTS is threatened by information leakage.Since our protocol has a secure quantum channel,all unauthorized users cannot obtain any information about the shared quantum state. So for an eavesdropper,he knows only the measurement results published by Alice and the players Bobi(i/=s′). In addition, owing to the quantum no-cloning theorem,the eavesdropper cannot obtain the quantum state by Charlie.
4.2.2. Participants’ attack
Compared with an eavesdropper, a player can destroy or steal the information through the participants’ attack, or the outside attack. The outside attack launched by a player will be regarded as the outside attack launched by an eavesdropper. And the analysis of the outside attack has been given in Subsubsection 4.2.1. This subsubsection is devoted to the participants’attack.
In our protocol, the players are divided into Charlie (the player who will reconstruct|Φ〉xy) and the players Bobi(i/=s′)who help Charlie.
Owing to the quantum no-cloning theorem, only Charlie can obtain|Φ〉xyin the end. For Charlie, he may want to reconstruct|Φ〉xywithout the help of other players Bobi(i/=s′).According to Eq.(10),after Alice and other players complete the measurements,Charlie’s density matrix is

4.3. Fairness
Owing to the unknown quantum state for the dealer Alice and the quantum no-cloning theorem, in the end, only one player Charlie can reconstruct|Φ〉xy. But instead of the dealer’s appointment,[36]Charlie is randomly elected by all players Bobi(1≤i ≤n+1)in each round. Therefore,Charlie’s generation event in our protocol is fair.
Theorem 1 If a player’s utility from cooperation is higher than the utility from cheat,this protocol achieves fairness.
Proof In this protocol,if a player deviates from the suggested strategy during executing the protocol,the protocol will not be aborted. But the cheating player cannot participate in this round nor the remaining rounds.
The player Bobi(1≤i ≤n+1)’s strategy in thejth round is taken for example, and the probability that this round is the revelation round is Pr(j=r) denoted byλ.When the player chooses to cheat, ifj=r, his utility is[1/(n+1)](U+c1-xΔ)+[n/(n+1)]Ub1. Ifj/=r, his utility

our protocol achieves fairness.
4.4. Correctness
Theorem 2 If all players in this protocol are rational,the protocol can achieve correctness.
Proof In this protocol, the players do not know the position of the real revelation roundr. On the one hand, if the players Bobi(i/=s′)send the wrong measurement results or remain silent in one round, they cannot participate in this round nor the remaining rounds. On the other hand,if Charlie,who reconstructs the quantum state in the revelation round,refuses to cooperate, his utility will be greatly reduced. In the rational quantum state protocol, as the players’ purpose is to maximize their utilities, no player will have an incentive to cheat. And eventually, Charlie will reconstruct the quantum state with 100%probability. Therefore,our protocol achieves correctness.
4.5. Strict Nash equilibrium

4.6. Comparison of results among protocols
The comparison of results among the protocols is shown in Table 1.

Table 1. Comparison of results among the protocols.
For the first condition“Whether the players are rational”,from a practical perspective,a player should be rational. In a rational protocol,a player will choose to participate in the protocol honestly or dishonestly based on his own utility. Therefore, the rational protocol is more practical with the actual situation. In Denget al.’s[15]and the other general QSTS protocols, a player is either an honest player or a dishonest player. On the contrary, in rational protocols, such as Maitraet al.’s,[37]Qinet al.’s,[39]Douet al.’s,[38]and ours,they start from themselves and judge how to choose strategies to maximize their own utilities.
For the second condition “Whether Alice knows the secret”, if Alice knows the shared quantum state, the protocol is like the remote preparation state. So Alice can clone the shares of the shared quantum state. Ultimately, not only one player can obtain the shared quantum state. In general,a dealer should be unknown to the shared quantum state, so only one player can obtain the shared quantum state,which is very much in line with the idea that multiple players share a quantum state. In Maitraet al.’s[37]and Qinet al.’s[39]protocols, Alice knows the information about the shared quantum state. While in Douet al.’s[38]protocol and ours, Alice does not know the information about the shared quantum state.
For the third condition“Whether Charlie is chosen by Alice”,if Charlie is chosen by Alice,it is unfair to other players,which may cause rational players to give up participating in the protocol. In Maitraet al.’s[37]protocol,Charlie is chosen by Alice. In Qinet al.’s[39]protocol, each player can obtain the shared quantum state,because the shared quantum state is known to the dealer Alice. While in Douet al.’s protocol[38]and ours, Charlie is elected by all the players, which ensures that every player has the same chance to become Charlie and thus making the protocol fair in Charlie’s election.
For the last condition “Whether Alice is online”, an online dealer Alice must interact with all players in each round,which leads to excessive information exchanging between the dealer and the players.A semi-off-line dealer Alice only needs to interact with the player twice. An off-line dealer Alice only needs to distribute the shares.[37]For a protocol with the semioff-line or off-line dealer,it reduces the information exchanging between the dealer and the players.[37]In Douet al.’s[38]and Qinet al.’s[39]protocols,the dealer is online. In Ref.[15],Denget al. respectively demonstrated a(t,n)RQSS protocol with the semi-off-line dealer and the off-line dealer. In our protocol,the dealer is of semi-off-line.
5. Conclusions and future work
In this work, we propose a rational quantum state sharing protocol with the semi-off-line dealer. In our protocol,the dealer Alice shares an arbitrary two-particle entangled state with the players by EPR pairs and GHZ states. Especially,the EPR pairs are prepared by Charlie. Compared with the preparation by the dealer,the preparation by Charlie can reduce the workload of the dealer. Meanwhile,each player has the same chance to become Charlie.In other words,Charlie is randomly elected by all players. Then, the fairness of the protocol is ensured. In addition,comparing with the quantum state sharing protocol with the online dealer,[38]the dealer appears only twice. Thus, the information about the shared quantum state cannot be directly provided for the players by the dealer.[37]Moreover,our protocol also proves to be correct and achieve a strict Nash equilibrium.
Our protocol is a non-hierarchical QSTS protocol. In fact, hierarchical QSTS protocol is a more general than nonhierarchical QSTS protocol.[10–14]In hierarchical QSTS protocol,since the players are in different grades,they have different capabilities to reconstruct the shared quantum state.Therefore, the future work that is worth doting is to investigate a hierarchical QSTS protocol in which the players are rational.
Acknowledgements
Project supported by the National Key Research and Development Program of China(Grant No.2020YFB1805405),the 111 Project, China (Grant No. B21049), the Foundation of Guizhou Provincial Key Laboratory of Public Big Data,China (Grant No. 2019BDKFJJ014), and the Fundamental Research Funds for the Central Universities, China (Grant No.2020RC38).
- Chinese Physics B的其它文章
- Erratum to“Boundary layer flow and heat transfer of a Casson fluid past a symmetric porous wedge with surface heat flux”
- Erratum to“Accurate GW0 band gaps and their phonon-induced renormalization in solids”
- A novel method for identifying influential nodes in complex networks based on gravity model
- Voter model on adaptive networks
- A novel car-following model by sharing cooperative information transmission delayed effect under V2X environment and its additional energy consumption
- GeSn(0.524 eV)single-junction thermophotovoltaic cells based on the device transport model

