Parameter estimation of continuous variable quantum key distribution system via artificial neural networks
Hao Luo(羅浩), Yi-Jun Wang(王一軍), Wei Ye(葉煒), Hai Zhong(鐘海),?,Yi-Yu Mao(毛宜鈺), and Ying Guo(郭迎),?
1School of Automation,Central South University,Changsha 410083,China
2School of Computer Science and Engineering,Central South University,Changsha 410083,China
3College of Applied Science,Jiangxi University of Science and Technology,Ganzhou 341000,China
Continuous-variable quantum key distribution(CVQKD)allows legitimate parties to extract and exchange secret keys.However,the tradeoff between the secret key rate and the accuracy of parameter estimation still around the present CVQKD system.In this paper,we suggest an approach for parameter estimation of the CVQKD system via artificial neural networks(ANN), which can be merged in post-processing with less additional devices.The ANN-based training scheme, enables key prediction without exposing any raw key.Experimental results show that the error between the predicted values and the true ones is in a reasonable range.The CVQKD system can be improved in terms of the secret key rate and the parameter estimation,which involves less additional devices than the traditional CVQKD system.
Keywords: quantum key distribution,artificial neural networks,secret key rate,parameter estimation
1.Introduction
Quantum key distribution (QKD)[1]enables two legitimate parts, Alice and Bob, to exchange secret keys through an insecure channel controlled by a potential eavesdropper,Eve.This technology can be combined with the classical onetime-pad cryptographic system, thereby providing information transmission with unconditional security.[2]There are two branches for QKD,i.e., continuous-variable (CV) QKD and discrete-variable(DV)QKD.Unlike the latter using the singlephoton resources(or detectors),[1]the former has the potential of high-key rate and low-cost implementations as it can be compatible with current standard telecom components such as homodyne and heterodyne detectors.[3]Over the past few years,achievements have been made for CVQKD in both theories and experiments.[4–13]The most mature CVQKD protocol is the prestigious Gaussian-modulated coherent state(GMCS)protocol,[4]which has been proved secure against collective attacks and coherent attacks.[14–17]In the GMCS protocol,Alice first encodes the secret key information by modulating the quadraturesxandpof coherent states with independent Gaussian distributions[18]and then sends them to Bob through an insecure quantum channel.After that, Bob proceeds homodyne detection (measures one of the two quadratures randomly) or heterodyne detection (measures both the two quadratures).[6,19–21]After the post-processing process that involves sifting, parameter estimation, reconciliation and privacy amplification,Alice and Bob share the correlated raw keys.
In order to estimate a bound on the maximum information that may have been eavesdropped by Eve, the channel transmittanceTand excess noise ξ need to be estimated.Traditional channel parameter estimation needs disclose parts of the raw keys.The more raw keys disclosed,the more accuracy the channel estimation would be.However, more disclosed raw keys leads to less capacity for carrying information,resulting in a lower secret key rate.Recent years, several works have been done on channel parameter estimation.For example, a parameter estimation was suggested for performance improvement of the CVQKD system,[22]which can be applied to low-Earth orbits and underwater communication scenarios by using the Monte Carlo approach.Chaiet al.proposed a parameter estimation method for implementation of the atmospheric GMCS CVQKD.[23]Guo[24]suggested a method for phase estimation and compensation of the CVQKD system,which can reconstruct the phase drifts even at low signal-to-noise ratio conditions.Wanget al.improved the accuracy of parameter estimation, realized by exchanging the order of parameter estimation and information reconciliation.[25]Yang suggested an improved four-state protocol in which the covariance matrix can be estimated from experimental data without using the linear channel assumption,guaranteeing its unconditional security in the asymptotical limits.[26]Liet al.considered an impact of denial-of-service attack on channel parameter estimation and suggested a method to prevent this attack.[27]However,the tradeoff between the secret key rate and the accuracy of parameter estimation is still unsolved.
In this paper, we propose an ANN-based parameter estimation scheme for performance improvement of the CVQKD system.In post-processing, Alice and Bob have to do some pretreatment to the raw keys(data dividing and normalizing),which are sequentially sent to the ANN for the training,aiming to learn the relationship between the initially prepared and received data.The ANN has the capacity of predicting all the data that Alice holds with few errors.Using this method,Alice and Bob can proceed estimation without disclosing any raw key to Eve.It can be used for the parameter estimation and attack prediction without heavily loading any additional devices,which is feasible to implement for the traditional CVQKD system.
This paper is organized as follows.In Section 2, we illustrate the framework of ANN-based parameter estimation scheme, and establish the ANN model for the CVQKD system.In Section 3, we show the performance of the ANNinvolved CVQKD system in terms of the secret key rate.In Section 4, the experimental results demonstrate the effect of the ANN-based parameter estimation scheme on the CVQKD system,including the secret key rate,the error range between the predicted values and the true values, as well as the relationship between the prediction accuracy and the block length.Finally,we make conclusions in Section 5.
2.ANN-based parameter estimation of CVQKD
For a traditional GMCS CVQKD protocol, it can be described as follows.Alice prepares the signal carriers with Gaussian modulation, which are sent to Bob through an unreliable quantum channel monitored by Eve.For the received signals, Bob proceeds the measurements by using homodyne or heterodyne detectors.Subsequently, Alice and Bob perform the data post-processing through an authenticated classical channel.As for the post-processing, Alice and Bob compare their encoding and measurement quadratures with each other and keep the data that they have performed with the same quadratures.By disclosing a subset of the raw keys, the parameter estimation is then proceeded to obtain an upper bound of the information that Eve can steal from.In the end, Alice and Bob could decorrelate their joint data from Eve via reconciliation and privacy amplification, while their data remain correlated.[28]The secret key rateKcan be given by

whereICis the mutual information between Alice and Bob,IEthe upper bound of information that Eve can obtain, andMthe amount of the information revealed during the postprocessing.
It is known that the post-processing has became a main restraint on the performance of CVQKD systems.Recently, the hardest issues have been devoted to parameter estimation,[23,25,29]reconciliation,[30–32]and privacy amplification,[33,34]but the tradeoff between the secret key rate and the accuracy of parameter estimation is still faced with challenges.
Fortunately, the ANN, known as the MP model,[35]is now a popular machine learning technique[36,37]based on the principle of neural networks in biology and network topology,aiming to process complex information by simulating nervous system of human brain.[38]It is an operational model composing a large number of nodes(neurons).In Fig.1(a), it shows the structure of a multiple-input neuron.Thej-th outputojreads

wherexiis thei-th input,wijis the weight ofxion thej-th path,bis bias that measures the difficulty of activation, and φ(·)represents the activation function.Figure 1(b)shows the structure of back propagation(BP)neural networks, which is employed in this paper.BP neural network is a multi-layer feed-forward neural networks, composed of input layer, hidden layer and output layer,the amount of the hidden layer can be one or more.
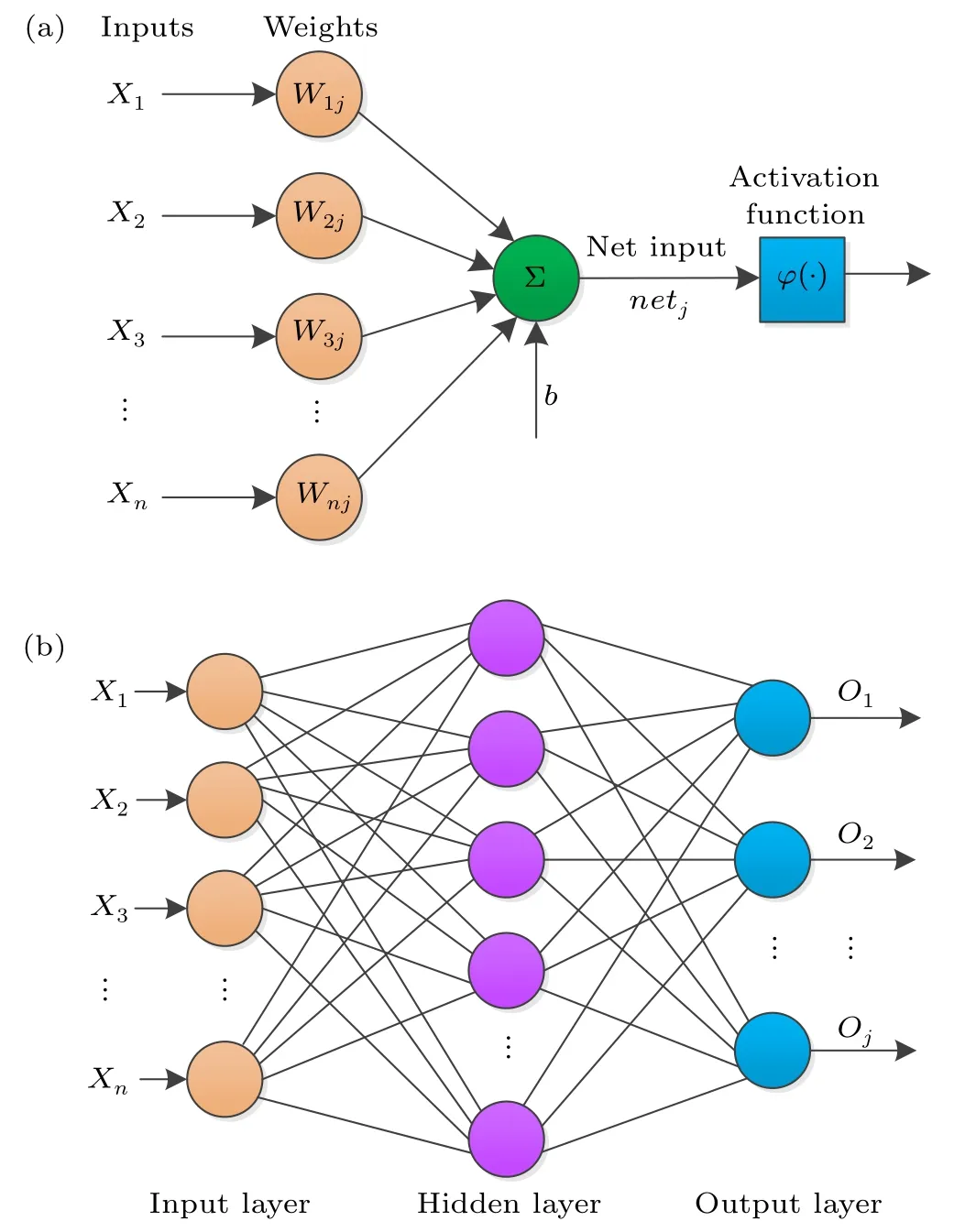
Fig.1.(a)Structure of a multiple-input neuron.(b)Structure of the BP neural networks.
The ANN-based CVQKD is shown in Fig.2.A set of coherent states,with desired modulation varianceVA,are prepared and multiplexed with the strong local oscillator(LO)by a polarization beam splitter.In the LO path, the delay line is employed to separate the LO from the signal in the time domain so that the time multiplexing can be realized.At the receiver,demultiplexing is executed by using polarization controller and polarization beam splitter.Through another delay line placed in the signal path, the delay of the LO due to the time multiplexing design is compensated so that both the signal and the LO can be precisely aligned.After Bob’s homodyne detection,Alice and Bob have two correlated sequencesxiandyi,respectively.Taking into account the additive white Gaussian noise(AWGN)channel,[39]xiandyican be related by

whereNis the total number of the raw keys,zirepresents Gaussian noise,xi~N(0,VA),t=√is the quantum channel loss with transmittanceT∈[0,1],zi~N(0,σ2), andyi~N(0,t2VA+σ2).Here η represents the efficiency of the detector,σ2=N0+ηTξ+Vel,N0is the variance of the shot noise,andVeldenotes the detector’s electronic noise.
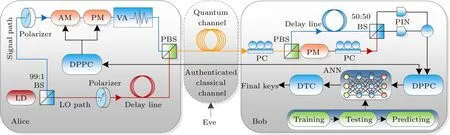
Fig.2.Schematic diagram of the ANN-based CVQKD system.LD: Laser diode.BS: Beam splitter; LO: Local oscillator; AM: Amplitude modulator; PM: Phase modulator; VA: Variable attenuator; PBS: Polarization beam splitter; PC: Polarization controller; PIN: PIN photodiode;DPPC:Data pre-processing center;Alice and Bob do pretreatment(including data dividing and data normalizing)to their own original data through their respective DPPC,then the data are transmitted through an authenticated channel.ANN:Artificial neural networks;DTC:Data terminal center,including reconciliation and privacy amplification.
For the parameter estimations, we take into account the transmittanceT, the excess noise ξ, and the maximum informationIE.Traditionally,we needs to disclose part of the raw keys,typically 50%,whereas in the proposed method none of the raw keys will be wasted.The ANN-based post-processing can be described as follows, it is worth noting that the data exchanged between Alice and Bob is achieved through the authentication channel, that is, the data may be eavesdropped,but cannot be tampered with.

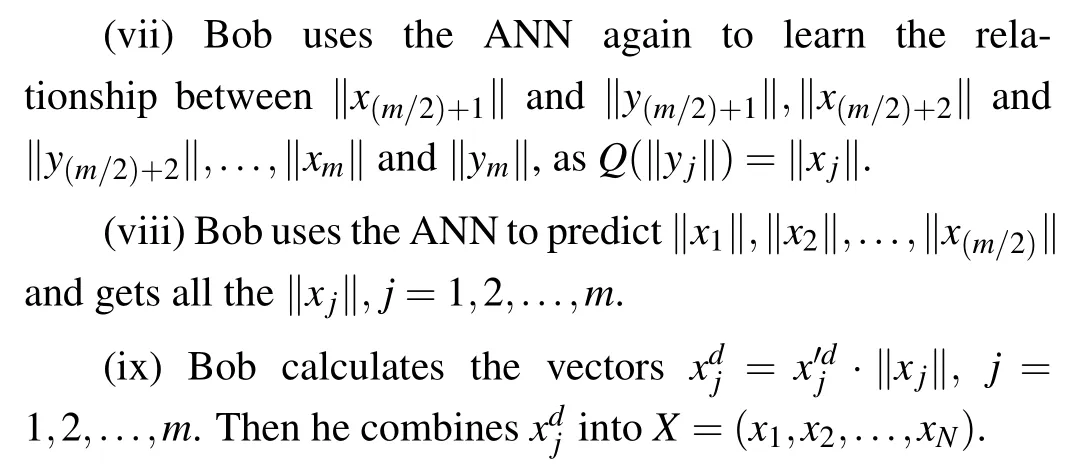
Theoretically, through the above-mentioned steps, Bob could have exactly all the sameXas Alice has.Then, along with his own raw keysY, he can proceed the parameter estimation without sacrificing any raw keys to the potential adversary, Eve.Consequently, Alice and Bob can achieve not only the high accuracy of parameter estimation but also the high secret key rate.But note that since the ANN algorithm is nothing more than an approximation of arbitrary function by learning the observed data and making prediction,it is impossible to obtain the completely correct results.Simply put,there are errors in the predicted data, which will lead to the deviation of parameter estimation, and eventually lead to the lower key rate than the ideal case.However, it is possible to achieve as high accuracy as possible by optimizing the structure of the ANN-involved CVQKD system and adjusting the suitable parameters.
3.Security analysis
After elaborating the schematic diagram of the ANNbased CVQKD system,we shall pay attention to the derivation of secret key rate.In the asymptotical case,[8]the key rate can be given by
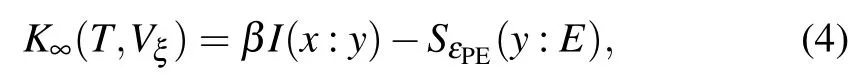
whereVξrepresents the variance of excess noise, β ∈[0,1]refers to the efficiency of the reconciliation,I(x:y)is the mutual information of Alice and Bob,(y:E) is the upper bound of information that Eve can obtain from Bob’s information, εPEis the probability that the true values of the parameters are not inside the confidence region.In order to ensure the security of the CVQKD system as much as possible without underestimating the eavesdropping,the worst case,that is,the case with the minimum key rate, needs to be considered.For this case,the minimum valueTminforTand the maximum valueshould be used.Then we can get the key rate in the finite-size case[39]
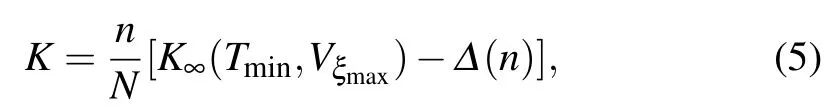
wherenis the amount of the raw keys used for key extraction,whilem=N?nraw keys can be used for estimation,and Δ(n)is related to the security of the privacy amplification(PA).The parameter Δ(n)has the form

where Hxis the Hilbert space of variablex,, and εPAare components of the failure probability of the whole CVQKD protocol.We assume dimHx=2, and a conservative value 10?10for.Thus,Δ(n)can be approximated as

Note although theoretically there is no raw key disclosed for parameter estimation in this scheme, it does not mean thatn=N(details will be shown in Section 4).In homodyne detection,I(x:y)can be derived from[40]
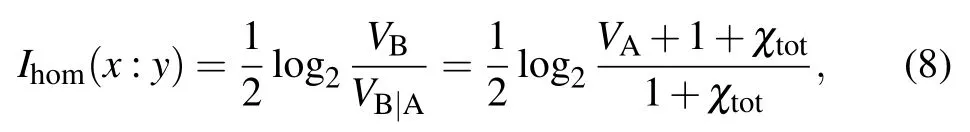
whereVBis Bob’s measured variance,VB|Ais the conditional variance, χtot= χline+χhom/Tminis the total noise,χline=1/Tmin?1+ξ is the channel-added noise,and χhom=[(1 ?η)+Vel]/η is detection-added noise.We note thatTmin=.
To acquiretminand, the maximum-likelihood estimatorsandcan be used for the transmission model of Eq.(3)
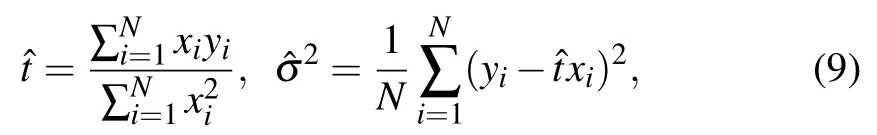
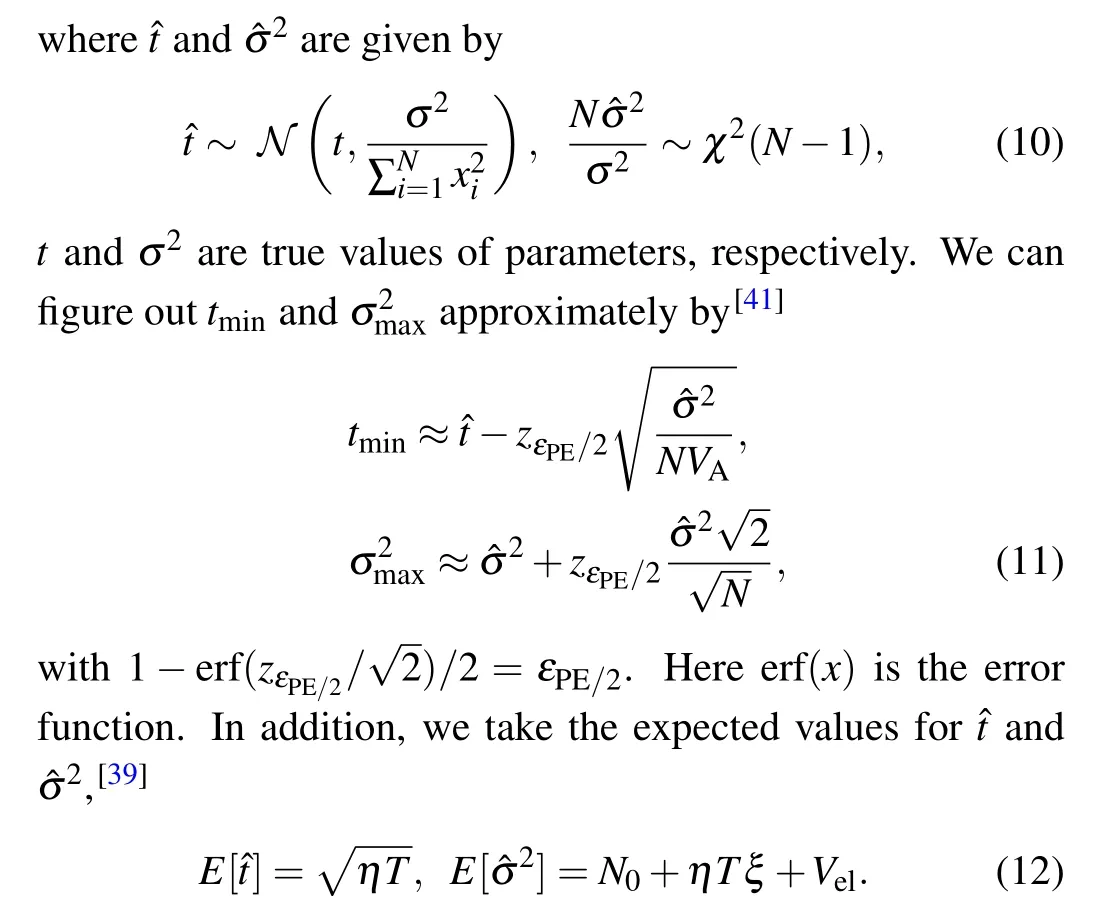
For the Holevo bound,[8]it can be simplified as
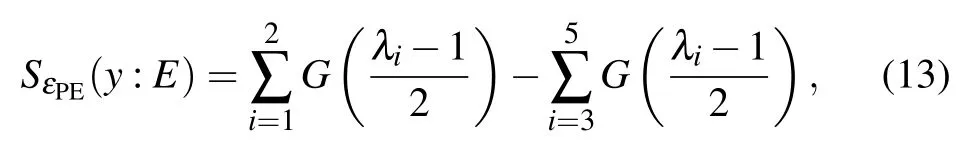
whereG(x)=(x+1)log2(x+1)?xlog2x, λiis symplectic eigenvalue of the corresponding covariance matrix given by(in homodyne detection case)
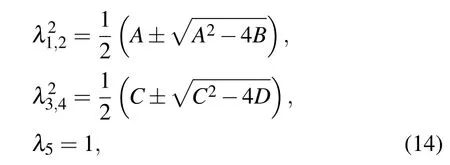
where we have
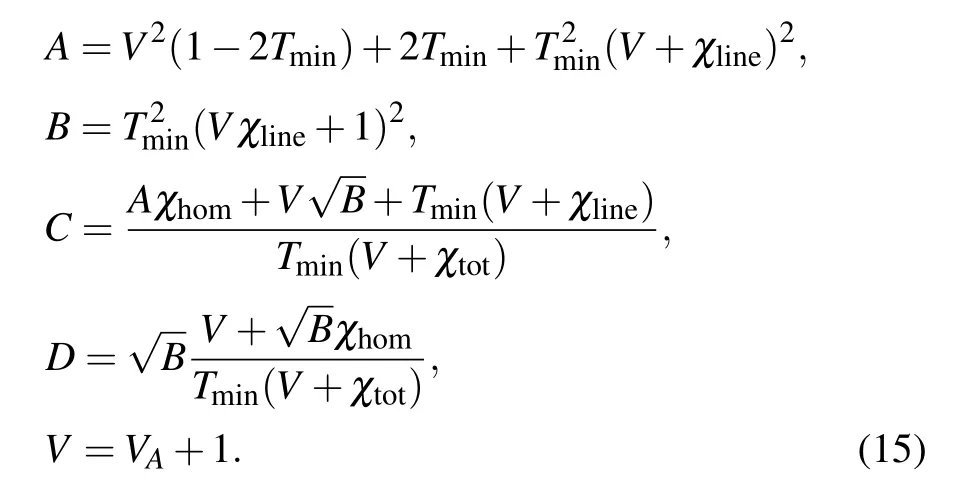
Using Eq.(9),the estimatorsandcan be derived.After substituting them into Eq.(11), we obtaintminand.Combining Eq.(8) with Eq.(13), we getIhom(x:y) and,and hence derive the secret key rateKfrom Eq.(5).
4.Numerical simulation
In the ANN-based scenario, the value ofn/Nshould be one in theory as no raw key is sacrificed.But it is impossible for the actual neural networks to make the predicted value exactly the same as the real one, meaning thatnis always less thanN.Therefore, it is still valid in Eq.(4) for this scheme except thatnrepresents the amount of Alice’s raw keys that predicted correctly by Bob.We take into account

which is the prediction accuracy.Then we have

The value ofn/Nis usually assumed to be 0.5 in our experiment, as in the traditional scheme.However, the value ofSdepends on the performance of the ANN.
We set the parameters of the ANN in Table 1,that is a BP neural networks which has a hidden layer with 12 neurons.In hidden layer,we take the activation function
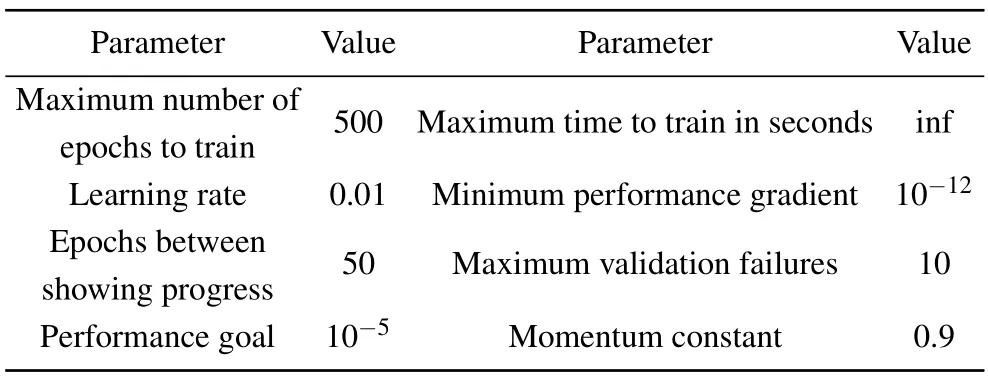
Table 1.Parameter settings.
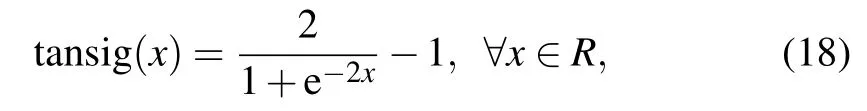
and the output layer activation function

As for the training function,we take the Levenberg–Marquardt algorithm, which is used for solving the non-linear least squares problems.These can minimize the problems arise in training process of the ANN.
At the beginning,all the variables and vectors are calculated and fed into the ANN,which randomly divides the data into three parts,i.e., training data, verification data, and test data, accounting for 70%, 15%,and 15%,respectively.After that, the networks begins to learn.The learning process will be repeated until the lowest level of error is achieved.(L=20 km,d=80,N=1.2×106).

Fig.3.Regression diagram of the first learning for
Figure 3 shows the regression graph of the first learning(for the relationship, while figure 4 represents the second learning(for the relationshipQ(‖yj‖)=‖xj‖).In these two graphs,the horizontal axis and the vertical axis represent the target value and the output value,respectively.Ideally,the output value should be equal to the target value,which is represented by a dotted line in the diagram.The black circles represent the data points,and the solid lines represent the fitting curves based on them.Theoretically,the closer the fitting curve is to the dotted line,the better the training effect of the ANN will be.After adequate training,the fitting curve of a perfect ANN should coincide with the “Y=T” curve, reflecting the most accurate description of the data relationship.But in reality,on the one hand,under the existing technology,such ideal ANN can not be constructed.On the other hand,if the fitting degree is too high(R=1),the overfitting occurs,that is, the training effect is perfect but the prediction effect is greatly deviated.During the two stages of training in our experiment, the fitting curve is close to the dotted line.The value ofRis greater than 0.8,meaning that the output and the target fit well.Besides,the values of minimum mean squared error(MSE)in two sequential training processes are relatively small,0.026163 and 0.023441,respectively.Both the regression diagram and the MSE reveal that the ANN is well trained.
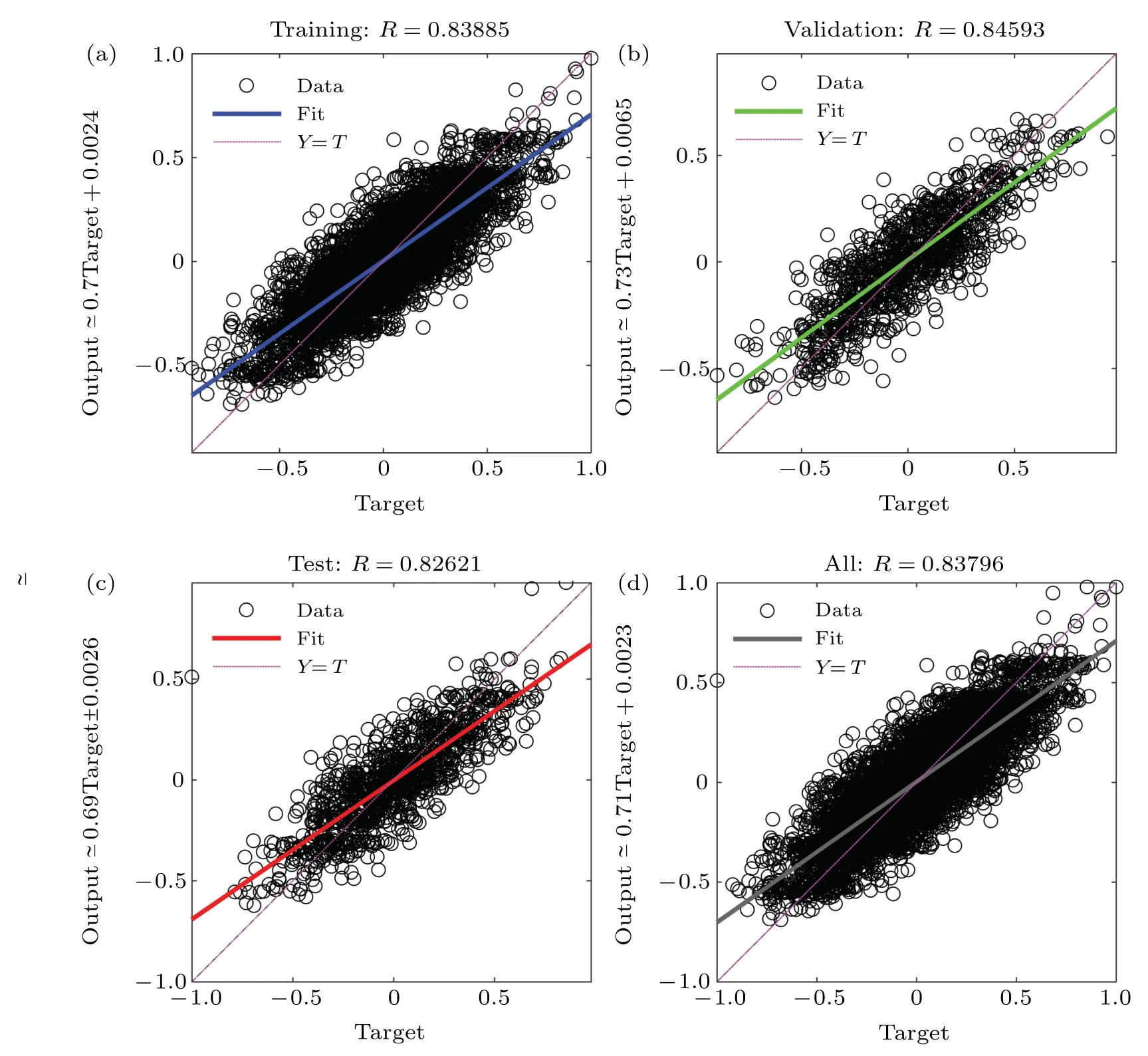
Fig.4.Regression diagram of the second learning for Q(‖yj‖)=‖xj‖(L=20 km,d=80,N=1.2×106).
After sufficient training, we began with the prediction process.To demonstrate the effect of the prediction, we randomly select some of Alice’s raw keys,and compare them with the predicted values.As shown in Fig.5,it shows that the two values are relatively close.In fact, the final mean relative error (MRE) we obtain from the experiment is 0.0246, which indicates that the prediction works well.
After Bob acquires all the predicted data (denoted asXout), the parameter estimation can be proceeded.In Fig.6,we performance of the ANN-based CVQKD system in terms of the secret key rate.ForS=1,it is the case of the ideal ANN scheme that the neural networks can predict all the data with complete accuracy.In addition, we also test the performance of secret key rate at different block lengths.We find that the ANN-based scheme has more advantages than the traditional one in terms of both transmission distance and secret key rate.The closer the value of prediction accuracySapproaches to 100%, the higher the secret key rate is, as shown in Eq.(17).The performance of the ANN-based scheme is closer to that of the ideal one,which results from the tunable parametern/N.
The improvement ofSdepends much on block length.Within certain range,prediction accuracy,as well as transmission distance, can be improved by the increased block length since more data provide the sufficient training.In Fig.7, we show effect of block length (blue-solid line) on the prediction accuracyS.For the block length that is no less than 106,the value ofSis between [80%,83%], whereas for the data length less than 106, a significant decrease of prediction accuracy can be observed, which indicates that adequate data are required for the performance improvement.In addition,due to the finite-size effect,small amounts of data may lead to the decrease of the secret key rate.However, when the block length is up to 107,Scan be improved slightly.The reason is that once there is enough data for the training, without optimizing the ANN, increasing data length makes no sense to improve the training and predicting ability of the ANN.As the growth of the block length, it takes more time in the training and predicting, which will be a great challenge for the real-time performance of the system.The time spent in the post-processing of CVQKD system via ANN depends on the structure of ANN itself, the algorithm of training and prediction,and the performance of the computer running ANN.The most important factor is the block length of the data.When the blocks length are 105,106,and 107,the times required to complete the post-processing are about two minutes, ten minutes and two hours,respectively.The performance of the computer used in our experiments is middling,with following configuration: core i5-10400F, 16G RAM, and 500G SSD.Obviously,The training time can be significantly reduced with a more powerful computer.In addition, during one working process of CVQKD system in optical fiber,the fitting relationship obtained by training the first data block can also be used in the subsequent data blocks.Therefore,we do not need to train every data block.Meanwhile,in Fig.7,we can also find that with the increase of transmission distance,the prediction accuracy gradually decreases.This is because the longer the distance,the more distorted the signal.
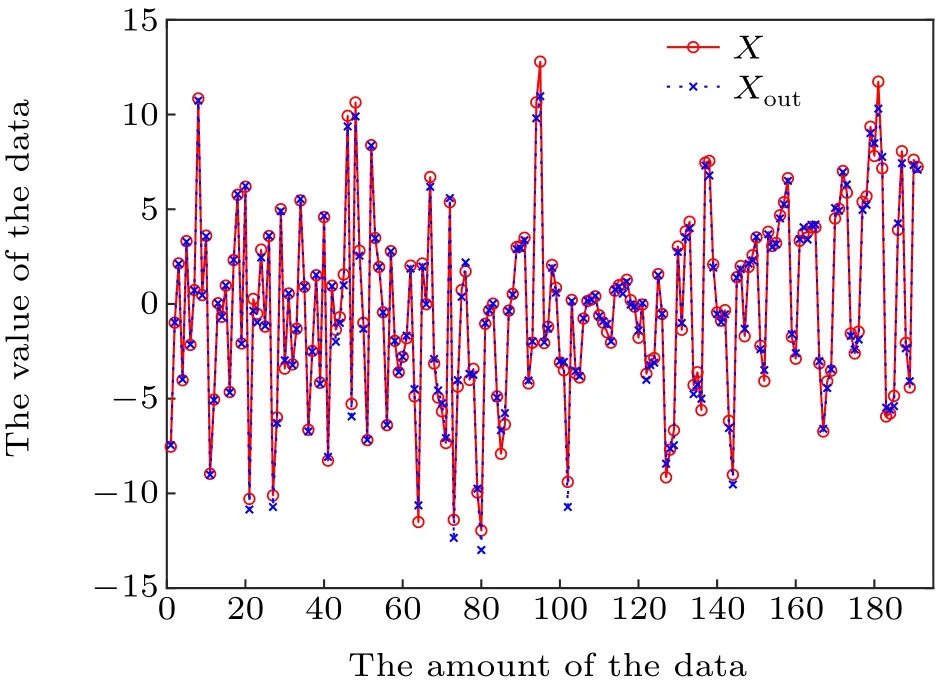
Fig.5.Comparison between X and Xout. X represents the true values of Alice’s raw keys, and Xout denotes the predicted values that Bob gets through the ANN.
In order to illustrate the characteristics of our scheme better, the method-of-moments (MM) scheme[42]and the transformed scheme by changing the implementation order of estimation and reconciliation(we call it exchanging order scheme for short)[25]are selected,to compare with our scheme.All of them can be used for the parameter estimations.The principles of these three schemes are completely different, our scheme uses a trained ANN to predict raw keys,while the MM scheme and the exchanging order scheme uses MM method to find a new estimator for σ2and changes the implementation order of parameter estimation and reconciliation, respectively.Compared with the other two competitors, our scheme is algorithmically simpler.In terms of disadvantages,more time is needed to train the networks in the ANN-based scheme, the performance of the estimator in the MM scheme is poor in minimizing variance and bias, and the exchanging order scheme requires an additional parameter estimation for channel characteristics, which increases the system complexity.And in terms of applicable scenario, our scheme is suitable for medium block length and unstable channel scenarios, while MM scheme is appropriate for long block length and high-loss channel, and the remaining scheme is applied to the stable system with slowly changing characteristics.Finally, we compared the secret key rates of the three schemes when the block lengthN=108and the transmission distanceL=30 km,there are 0.0507,0.085,and 0.036,respectively.It is important to note that this is not the best performance of our scheme,we can increase the key rate by improving the structure of the neural networks, adjusting the parameters’value,and optimizing the training and predicting algorithm.For example, instead of BP neural networks, we can use the radial basis function (RBF) neural networks, which contains input layer,hidden layer(only one)and output layer.Various forms of RBF function can be used as the activation function in hidden layer, take Gaussian function for example, its expression can be written as follows:
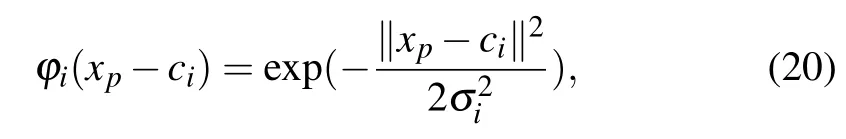
where φi(·)represents thei-th RBF function,xpis thep-th input,cirepresents the center ofi-th node in the hidden layer,andis the variance of the Gaussian function.Then thej-th output of the RBF neural networks reads

wherewijis the connection weight of the hidden layer to the output layer.Compared with BP networks,RBF networks can approximate arbitrary function with higher precision.Our experiments show that the key rate can be increased by 3% or even more by using the RBF networks and selecting appropriate parameters, such as the dimension of the input data,the spread of radial basis function, and so on.It should be noted that although RBF networks can avoid the local minimum problem and thus achieve higher prediction accuracy,its structure can be more complex.Since there is no specific law to follow in neural networks design at present,quite a lot of continuous attempts are essential to improve the key rate.We believe that different approaches,or combinations of them,may lead to better performance.In general, although the key rate of the ANN-based scheme is not the highest,the complexity of the algorithm is low, and additional hardware is barely required.The property that ANN can approach any rational number in theory makes it have the most prominent advantage, that is, suitable for the complex, variable and unstable channels.
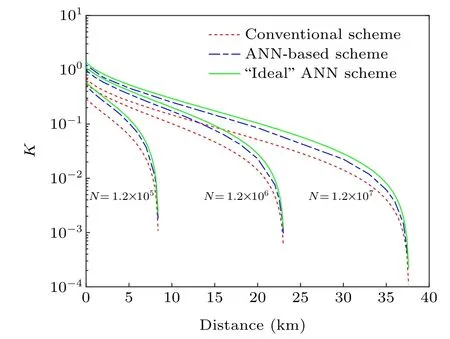
Fig.6.Secret key rate as a function of transmission distance.From left to right,red-dotted lines,blue-dashed lines,and green-solid lines,correspond to the traditional scheme,the ANN-based scheme,and the ideal ANN scheme,respectively.

Fig.7.The A–N curve shows how the prediction accuracy varies with the length of the data(blue-solid line,L=20 km).The A–L curve represents the variation of the prediction accuracy with transmission distance (red-dotted line,N=1.2×107).
5.Conclusion
We have presented an ANN-involved parameter estimation scheme for performance improvement of the CVQKD system,where BP neural networks are placed in the data postprocessing stage without disclosing the raw keys.After being preprocessed,Alice’s and Bob’s original data are fed into the ANN to start the training experiments, in which the structure and the parameters of the ANN are constantly adjusted until the regression curve and error curve show that the ANN has achieved its best performance.Relationship between the data is obtained at the end of the training experiments before the ANN’s prediction.It is secure from Eve’s eavesdropping since none of the original data is disclosed.Simulation results suggest that the ANN-based scheme has shown better performance in the parameter estimation, secret key rate, capacity for carrying information and the accuracy of prediction,compared with the traditional scheme and other schemes.Besides,the ANN-based scheme,which requires very few additional devices,can be expediently implemented in the practical CVQKD systems.
- Chinese Physics B的其它文章
- A broadband self-powered UV photodetector of a β-Ga2O3/γ-CuI p-n junction
- High-sensitive terahertz detection by parametric up-conversion using nanosecond pulsed laser
- High efficiency,small size,and large bandwidth vertical interlayer waveguide coupler
- High-fidelity resonant tunneling passage in three-waveguide system
- An analytical model for cross-Kerr nonlinearity in a four-level N-type atomic system with Doppler broadening
- Determine the physical mechanism and source region of beat wave modulation by changing the frequency of high-frequency waves